Yep you need to do this if you want the darn thing to work. But just like your LAN rule, you can make this as open or as restrictive as you want. Here you can limit the PPTP users to accessing only specific hosts on specific ports, or open it all up. We are going to assume you want full access for your PPTP users so we are going to setup a firewall rule that is exactly like the default LAN rule.
Start by clicking “Rules” under the firewall section of the m0n0wall interface.
Next click any of the “+” Icons on the screen so we can add a new rule.
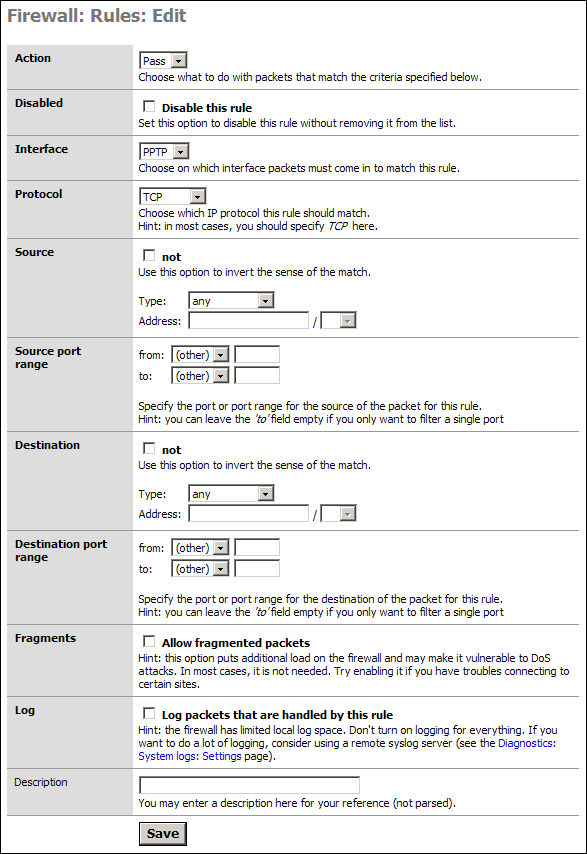
As stated we are going to allow all our PPTP users to access all parts of the LAN, WAN, etc. If you wish to limit this access then you will need to modify things accordingly. I will present one example of such a rule after this default section.
Simply go to the “Interface” section and select PPTP from the drop down. In the Description put something meaningful like “Default PPTP -> any.”
Click Save
You will have to Apply the changes on the next screen.
You are now done setting up the PPTP Server!
In some cases, most for those people who are granting PPTP access to others they do not fully trust, you will want to limit access (Specific Allow Rules) or mitigate specific access with Deny Rules. With specific allow users would be granted explicit permission to access hosts, and sometimes specific ports, and all other traffic is denied. The latter would be done if you wanted the PPTP clients to access the LAN & WAN but did not want them to access your SAMBA server for instance.
Our example is an allow rule granting permission for people on the PPTP network to use SSH on a LAN server with the IP address 192.168.1.151:
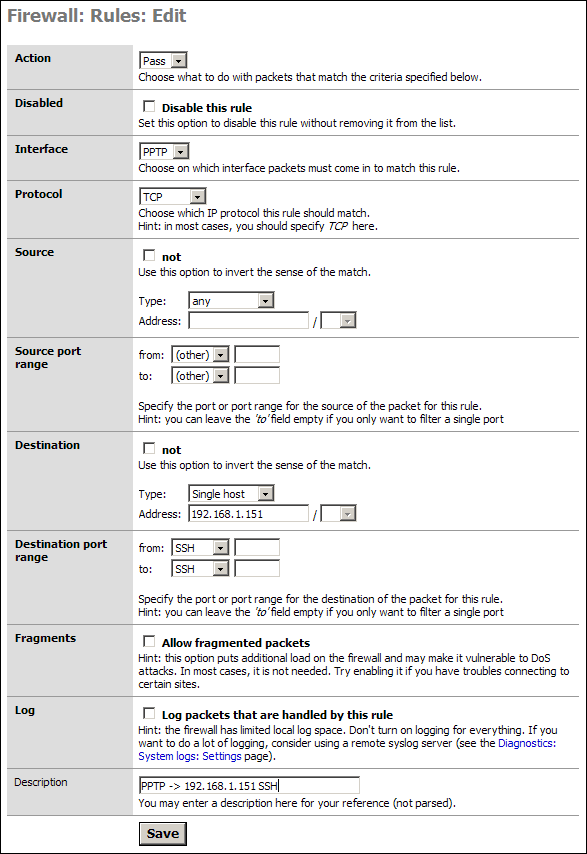
Save and Apply these rules as needed. Test them all to make sure they are working as designed. Most networks are compromised because no one checked the ACLs were activated or even working properly.