Table of Contents
- 15.1. How do I setup mobile user VPN with IPsec?
- 15.2. How can I prioritize ACK packets with m0n0wall?
- 15.3. Why isn't it possible to access NATed services by the public IP address from LAN?
- 15.4. I enabled my PPTP server, but am unable to pass traffic into my LAN
- 15.5. I just added a new interface to my m0n0wall box, and now it doesn't show up in the webGUI!
- 15.6. Does m0n0wall support MAC address filtering?
- 15.7. Does m0n0wall support SMP systems?
- 15.8. Why can't hosts on a NATed interface talk to hosts on a bridged interface?
- 15.9. What were the goals behind the m0n0wall project?
- 15.10. How do I setup multiple IP addresses on the WAN interface?
- 15.11. Can I filter/restrict/block certain websites with m0n0wall?
- 15.12. Why are some passwords stored in plaintext in config.xml?
- 15.13. Are there any performance benchmarks available?
- 15.14. What about hidden config.xml options?
- 15.15. Why can't I query SNMP over VPN?
- 15.16. Can I use m0n0wall's WAN PPTP feature to connect to a remote PPTP VPN?
- 15.17. Can I use multiple WAN connections for load balancing or failover on m0n0wall?
- 15.18. Can I access the webGUI from the WAN?
- 15.19. Can I access a shell prompt?
- 15.20. Can I put my configuration file into the m0n0wall CD?
- 15.21. How can I monitor/graph/report on bandwidth usage per LAN host?
- 15.22. Will there ever be translated versions of m0n0wall? Can I translate m0n0wall into my language?
- 15.23. Does m0n0wall support transparent proxying?
- 15.24. Should I use m0n0wall as an access point?
- 15.25. Why am I seeing traffic that I permitted getting dropped?
- 15.26. How can I route multiple subnets over a site to site IPsec VPN?
- 15.27. How can I block/permit a range of IP addresses in a firewall rule?
- 15.28. Why does my MSN Messenger transfer files very slowly when using traffic shaper?
- 15.29. Can I forward broadcasts over VPN for gaming or other purposes?
- 15.30. How can I use public IP's on the LAN side? Or how can I disable NAT?
- 15.31. Are PCMCIA cards supported?
- 15.32. Are there any tweaks for systems that will need to support large loads?
- 15.33. Can I add MRTG or some other historical graphing package to m0n0wall?
- 15.34. Can Captive Portal be used on a bridged interface?
- 15.35. Can I run Captive Portal on more than one interface?
- 15.36. Why do my SSH sessions time out after two hours?
- 15.37. Why isn't the reply address of the list set to the list?
- 15.38. Why am I seeing "IP Firewall Unloaded" log/console messages?
- 15.39. Why can't my IPsec VPN clients connect from behind NAT?
- 15.40. Why doesn't m0n0wall have a log out button?
- 15.41. Can I have more than 16 simultaneous PPTP users?
- 15.42. Can I sell m0n0wall (or use it in a commercial product)?
- 15.43. Where can I get a high-resolution version of the m0n0wall logo?
- 15.44. When will m0n0wall be available on a newer FreeBSD version?
- 15.45. Is there any extra Captive Portal RADIUS functionality available?
- 15.46. How can I increase the size of the state table?
Everything you ever wanted to know about m0n0wall but were afraid to ask. This is a must-read before posting questions to the mailing list!
This tutorial tries to explain how to setup mobile user IPsec VPN with m0n0wall and Windows clients that use SafeNet SoftRemoteLT, a popular IPsec VPN client. You need m0n0wall pb25 or later for mobile user VPN.
Log into your m0n0wall and go to the IPsec: Mobile clients page.
-
Configure the settings as shown in the following picture:
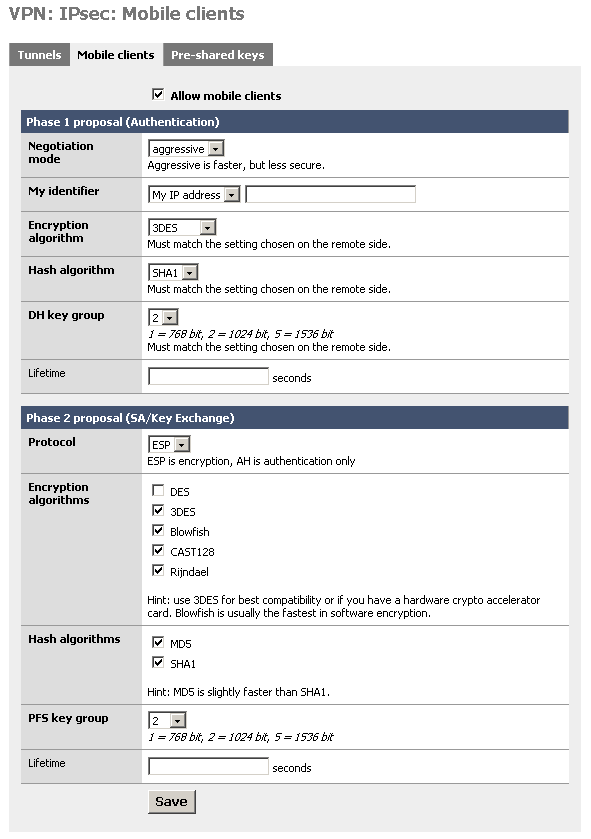
You must use aggressive mode, as only IP addresses can be used as identifiers in main mode.
Click "Save", then go to the IPsec: Pre-shared keys page.
Add a new key for each mobile user (use different keys, and at least 8 characters!). Use the e-mail address of the corresponding user as the identifier.
Go to the IPsec: Tunnels page, check "Enable IPsec" and click "Save".
This example assumes version 10 of SafeNet SoftRemoteLT.
Install SafeNet SoftRemoteLT, if not already installed, and reboot.
Right-click on the SoftRemote icon next to the clock and select "Security Policy Editor".
Choose Edit -> Add -> Connection.
-
Configure the connection properties as follows:
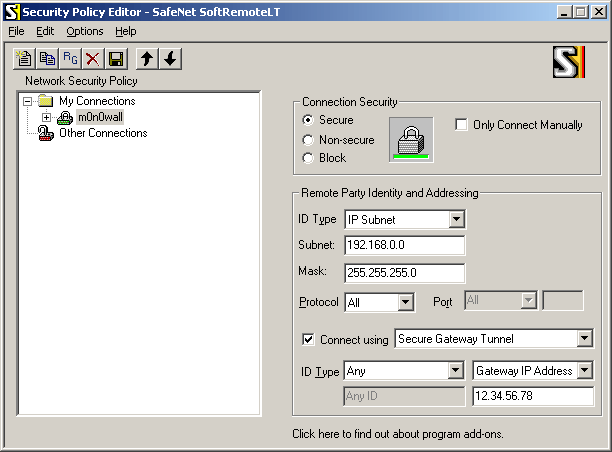
Insert your LAN subnet + mask and enter the external IP address (or hostname) of your m0n0wall instead of "12.34.56.78".
-
Select "Security Policy" and use the following settings:
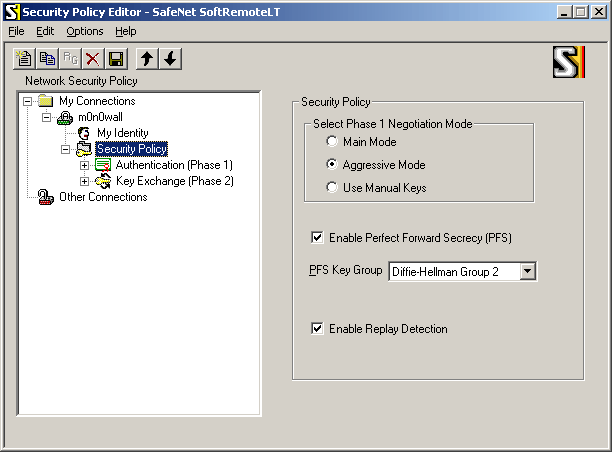
-
Select "My Identity" and use the following settings:
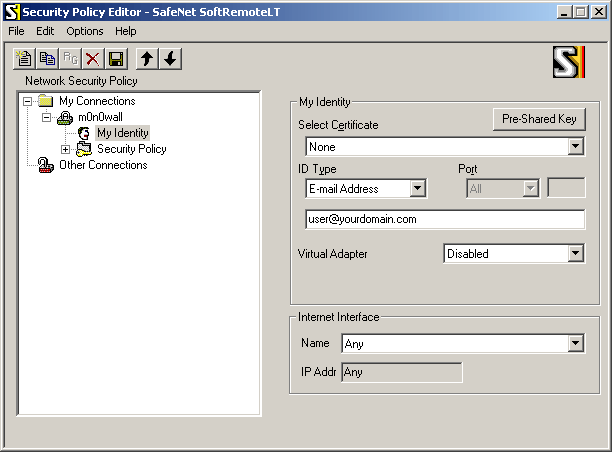
Enter the user's e-mail address, then click the button "Pre-Shared Key" and enter the pre-shared key. The e-mail address (and pre-shared key) must correspond with an entry on the IPsec: Pre-shared keys page on m0n0wall.
-
Select "Authentication (Phase 1) -> Proposal 1" and use the following settings:
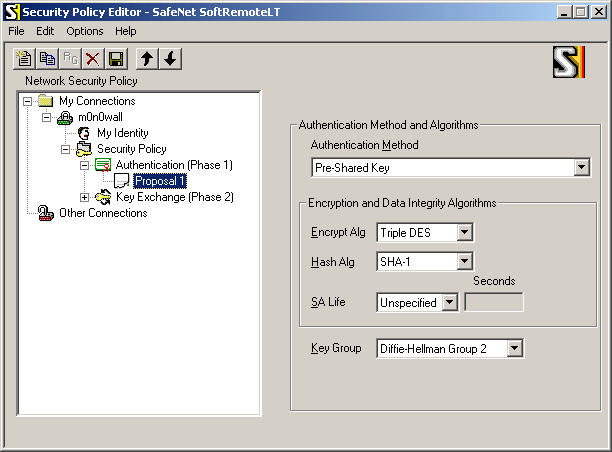
-
Select "Key Exchange (Phase 1) -> Proposal 1" and use the following settings:
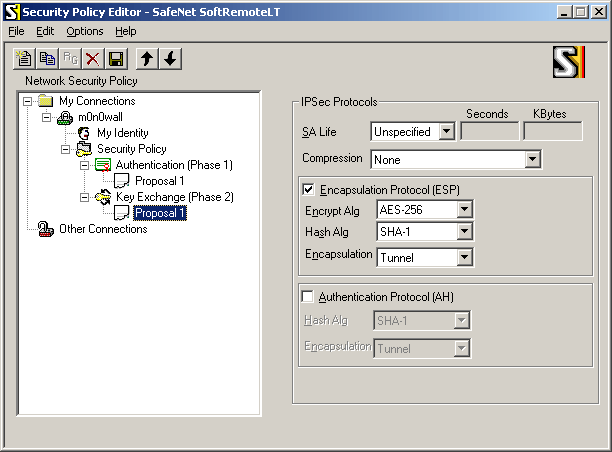
If you have a crypto accelerator card in your m0n0wall, you may want to use Triple DES instead of AES-256 as the encryption algorithm (some crypto accelerators do not support AES).
Choose File -> Save.
If you have a crypto accelerator card in your m0n0wall, you may want to use Triple DES instead of AES-256 as the encryption algorithm (some crypto accelerators do not support AES).
Choose File -> Save.
Make sure that the Internet connection is established. Try to ping a host on your LAN (e.g. your m0n0wall's LAN IP address). The first few pings will time out as it takes a few seconds for the IPsec tunnel to be established. Use SoftRemote's log viewer and connection monitor to tell you what's going on (right-click on the SoftRemote icon next to the clock to open them).